Category: INSIGHTS
Inside Flame: You Say Shell32, I Say MSSECMGR
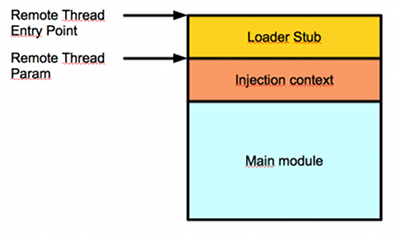
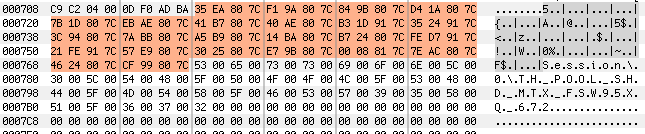
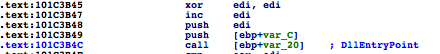
explorer.exe than winlogon.Shell32.dll in this case.LoadLibrary, to avoid being detected as an active module.DDEnumCallback is called, Flame injects a blob and creates a remote thread in Services.exe. The blob has the following structure:dllloader.cpp[2] with some additional tricks.The injection context is a defined structure that contains all the information the loader stub may need including API addresses or names, DLL names, and files—in fact, the overall idea reminded me of Didier Stevens’ approach to generating shellcodes directly from a C compiler[3]
Injection Context: Blob + 0x710
API Addresses:
|
esi OpenMutexW
esi+4 VirtualAlloc
esi+8 VirtualFree
esi+0Ch VirtualProtect
esi+10h LoadLibraryA
esi+14h LoadLibraryW
esi+18h GetModuleHandleA
esi+1Ch GetProcAddress
esi+20h memcpy
esi+24h memset
esi+28h CreateFileMappingW
esi+2Ch OpenFileMappingW
|
esi+30h MapViewOfFile
esi+34h UnmapViewOfFile
esi+38h ReleaseMutex
esi+3Ch NtQueryInformationProcess
esi+40h GetLastError
esi+44h CreateMutexW
esi+48h WaitForSingleObject
esi+4Ch CloseHandle
esi+50h CreateFileW
esi+54h FreeLibrary
esi+58h Sleep
esi+5Ch LocalFree
|
Shell32.dll: A matter of VAD
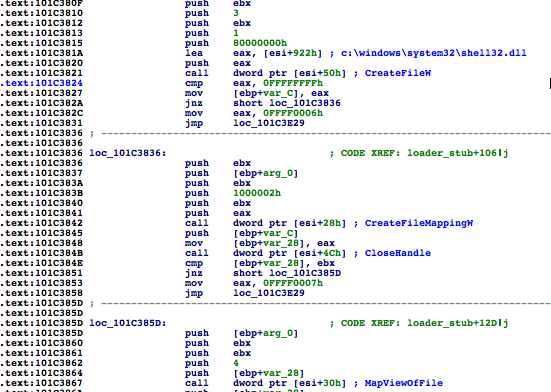
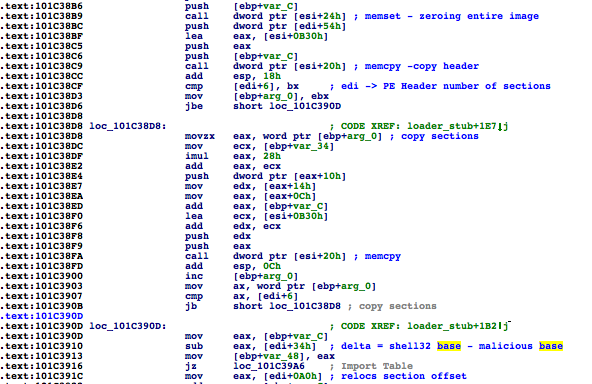
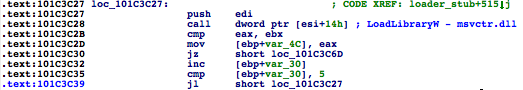
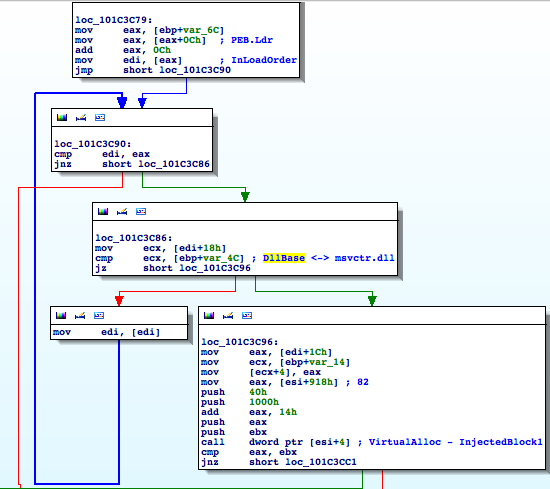
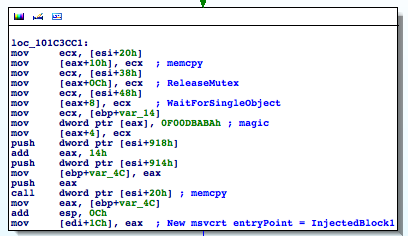
Shell32.dll, which is one of the largest DLLs you can find on any Windows system, meaning it’s large enough to hold Flame across different versions.shell32.dll has been mapped, a VAD node is created that contains a reference to the FILE_OBJECT, which points to Shell32.dll. Flame then zeroes that memory and loads its malicious module through the custom PE loader, copying sections, adjusting permissions, and fixing relocations.Shell32.dll, a trusted module, when it’s actually mssecmgr.ocx.DllEntryPoint, passing in DLL_PROCESS_ATTACH to initialize the DLL.DLL_THREAD_ATTACH, DLL_THREAD_DETACH, and DLL_PROCESS_DETACH.msvcrt.dll is loaded up to five times, which is a little bit weird, no?InLoadOrder structure is traversed to find the entry that corresponds to msvcrt.dll by comparing the DLL base addresses:InjectedBlock1 (0x101C36A1) is a small piece of code that basically dispatches the events received to both the malicious DLL and the original module. msvcrt.dll several times to increase its reference count to prevent msvcrt.dll from being unloaded, since this hook would then become useless.Thoughts on FIRST Conference 2012
I recently had the opportunity to attend the FIRST Conference in Malta and meet Computer Emergency Response Teams from around the world. Some of these teams and I have been working together to reduce the internet exposure of Industrial Control Systems, and I met new teams who are interested in the data I share. For those of you who do not work with CERTs, FIRST is the glue that holds together the international collaborative efforts of these teams—they serve as both an organization that makes trusted introductions, and vets new teams or researchers (such as myself).
Old Tricks, New Targets
Just a few days ago, Digitalbond announced that they had been victims of a spear phishing attack. An employee received an email linking to a malicious zip file, posing as a legitimate .pdf paper related to industrial control systems security. Therefore, the bait used by the attackers was supposedly attracting targets somehow involved with the ICS community. (more…)
Summercon 2012
I started attending in 2000 when it was in Atlanta, GA and had a fantastic time. Over the years, the conference has changed and organizational efforts have varied, as running a conference is quite subjective and provides little utility (at times). Around 2006, the changing of the guard happened once again, leaving Mark and me the new organizers of the con. Like others that came before us, we put our own touch on the conference and have probably strayed further from the original than any before us.
QR Fuzzing Fun
QR codes [1] have become quite popular due to their fast readability and large storage capacity to send information. It is very easy to find QR codes anywhere these days with encoded information such as a URL, phone number, vCard information, etc. There exist tons of apps on smartphones that are able to read / scan QR codes.
|
Platform
|
Popular QR Apps / Libraries
|
|
Android
|
· Google Goggles
· ZXing
· QRDroid
|
|
iOS
|
· Zxing
· Zbar
|
|
BlackBerry
|
· App World
|
|
Windows Phone
|
· Bing Search App
· ZXlib
|
QR codes are very interesting for attackers as they can store large quantity of information, from under 1000 up to 7000 characters, perfect for a malicious payload, and QR codes can be encrypted and used for security purposes. There are malicious QR codes that abuse permissive apps permissions to compromise system and user data. This attack is known as “attagging”. Also QR codes can be used as an attack vector for DoS, SQL Injection, Cross-Site Scripting (XSS) and information stealing attacks among others.
ST19XL18P – K5F0A Teardown
4 Metal, 350 nanometer fabrication process, EAL4+ smart card. A device fabricated in 2002 and yet, today the latest ST19W/N series only main differences are the ROM data bus output width into the decrypt block and the fabrication process (180nm and 150nm shrink).
The device was dipped into a HydroFluoric (HF) bath until the active shielding fell off. The result of this saved about 10 minutes of polishing to remove the surface oxide and Metal 4 (M4). This also helps begin the polishing process on the lower layers fairly evenly.
The oxide thickness of a layer once the passivation oxide is removed requires less than 2 minutes per layer to remove. We purposely stop just before the Metal 3 (M3) surface is exposed leaving the vias visibly clear (there are several gates tied to the ground of the mesh on Metal 4 (M4) as well as the active shield’s begin and end vias.
As Metal 3 (M3) was removed exposing the M2 layer, the device is beginning to not look so complicated.
Metal 1 (M1) shows us all the transistors. We did not polish down to the poly. Most of the gates are understandable without it for the purposes of finding the clear data bus.
Most likely, these NVM areas in Figure 7 & 8 are trimming or security violation related. No further investigation is planned on these areas (it isn’t necessary).
#HITB2012AMS: Security Bigwigs and Hacker Crème de la Crème Converge in Amsterdam Next Week
Back. The man who first brought Microsoft Windows to its knees in 2003 as part of the LSD Group and later became the world’s first to present a successful and widespread attack against the mobile Java platform is back at HITBSecConf! This time he will demonstrate the first ever successful attack against digital satellite set–top–box equipment implementing the Conax Conditional Access System with advanced cryptographic pairing function. Yes, we’re talking major security flaws in digital satellite TV set-top-boxes and DVB chipsets used by many satellite TV providers worldwide.
More Labs / More Signal Intelligence
Enter the Dragon(Book), Pt 2
|
typedef struct _copper
{
char field1[0x7fffffff];
char field2[0x7fffffff];
char pad0;
char pad1;
} copper, *pcopper;
int main(int argc, char **argv)
{
copper david;
printf(“sizeof david = %xn”, sizeof(david));
printf(“sizeof david’s copper.field1 = %xn”, sizeof(david.field1));
if(argc > 1 && strlen(argv[argc-1]) < sizeof(david.field1))
strncpy_s(david.field1, argv[argc-1], sizeof(david.field1));
return 0;
}
|
|
sizeof david = 1
sizeof david.copper.field1 = 7fffffff
|
Thoughts on AppSecDC 2012
- Pentesting Smart Grid Web Apps from Justin Searle
- Vulnerabilities in Industrial Control Systems from ICS-CERT
- AMI Security from John Sawyer and Don Weber
- Project Basecamp: News from Camp 4 from Reid Wightman
- Denial of Service from Eireann Leverett
- Securing Critical Infrastructure from Francis Cianfrocca