Guest blog by Urban Jonson, SERJON
with John Sheehy and Kevin Harnett
During my recent presentation at ESCAR USA, I shared findings from my latest research on the automotive industry’s adoption of Threat Analysis and Risk Assessment (TARA) processes to develop cybersecurity artifacts that align with regulatory requirements. The automotive TARA is a systematic process used to identify potential cybersecurity threats to vehicle systems, evaluate their likelihood and impact, and determine appropriate mitigations to reduce risk to acceptable levels.
One key insight derived across numerous TARA exercises is that many organizations struggle with consistency and accuracy in their internal cybersecurity documentation. To address this, I recommend thoroughly analyzing the workflows involved in creating, reviewing, and approving such documentation. By applying business process reengineering principles and best practices, organizations can streamline and strengthen these workflows.
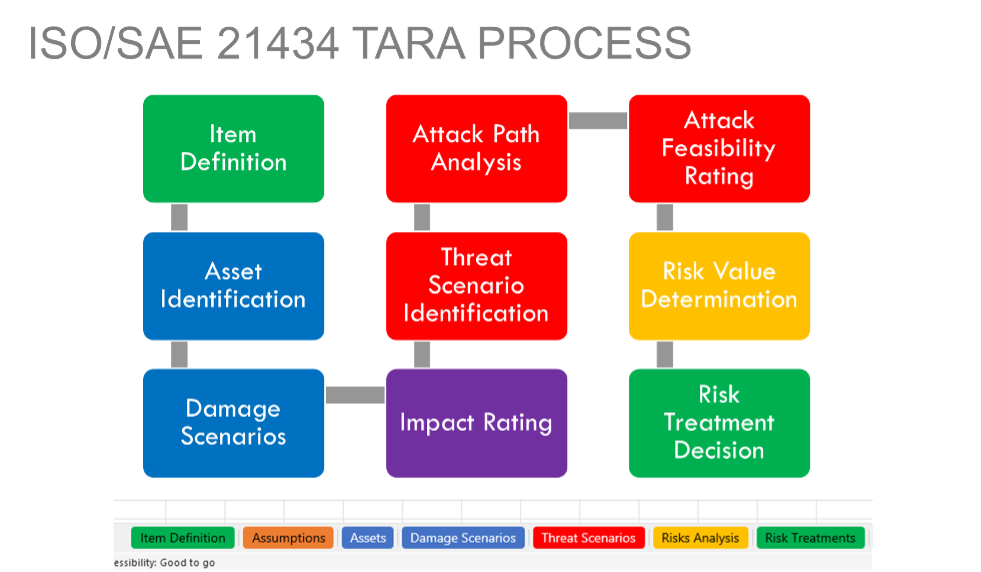
These findings also highlight a broader pattern that we have observed across the gamut of industries, from automotive to energy to software development, and all points in between.
In our experience working with companies of all sizes and types, one challenge keeps coming up: cybersecurity operations are becoming more expensive, but not necessarily more effective. Too often, we see teams overwhelmed by alerts, buried in redundant tools, and unsure whether their efforts are aligned with real threats. If this sounds familiar, there’s a better way to approach it—one that blends deep knowledge of threat behavior, innovative process design, and focused spending. And yes, sometimes it means bringing in an outside perspective like ours to get things moving in the right direction.
Starting with Real Threat Intelligence: TTPs
When we start working with a company, one of the first things we look at is how well its cybersecurity efforts align with actual risks. We use industry-specific TTPs—Tactics, Techniques, and Procedures used by real attackers in that sector—to uncover what’s really at stake. For example, in finance, phishing and credential theft are huge; ransomware targeting OT environments is more common in manufacturing.
This isn’t just threat modeling, it’s about making sure the company’s cybersecurity operations are focused on what matters. We’ve seen companies spend big on fancy cybersecurity tools that protect against unlikely scenarios, while overlooking common, costly vulnerabilities. TTPs help us steer the conversation toward high-impact areas that deserve real attention.
Reengineering Cyber Processes That Drag Companies Down
With those threat patterns in mind, we conduct a process analysis to map the way cybersecurity workflows actually operate inside the business. Are patching cycles too slow? Are incidents managed the same way across departments? Are cybersecurity tools overlapping or underutilized?
This is where business process reengineering comes in. We work with teams to strip away complexity, redesign inefficient workflows, and introduce automation or clear accountability where needed. The goal is simple: make the company’s cybersecurity operations faster, smarter, and cheaper without compromising protection.
And we get it—internal teams are often too close to the process to spot the friction. That’s why companies bring us in. We bring an external lens, ask the hard questions, and get everyone aligned on a working strategy.
The Eisenhower Matrix: A Surprisingly Useful Budget Tool
Once we’ve got processes in better shape, it’s time to review technology spending. One of the tools we like to use is the Eisenhower Matrix, which enables us to categorize every cybersecurity investment:
- Urgent and Important: Must-haves, like tools protecting your most targeted assets
- Important but Not Urgent: Strategic efforts, like employee training or improving logging infrastructure
- Urgent but Not Important: Fire-drill requests that burn budget but add little value
- Neither Urgent nor Important: Legacy tools collecting dust (and invoices)
This simple framework helps leadership make clearer, faster decisions, and we help drive those conversations with data and context.
Why Bringing in a Consultant Helps
You might wonder, “Why bring in an outside firm to do this?” The answer is that a security consultancy with seasoned experts offers speed, experience, and perspective. We’ve worked with multiple industries, seen common patterns and pitfalls, and can move faster than most internal teams alone. We’re not here to replace your cybersecurity team; our job is to make them more effective.
If you’re serious about reducing costs, boosting productivity, and ensuring your cybersecurity efforts match your business needs, let’s talk. A little outside perspective might be just what your company needs to move forward with clarity and confidence.
Urban Jonson is a co-founder of SERJON (www.serjon.com) and a frequent collaborator with IOActive. Urban is a cybersecurity industry leader and serves in multiple advisory roles, including SAE International, TMC, ESCAR USA, CyberTruck Challenge, and as a cybersecurity expert for FBI InfraGard and the FBI Automotive Sector Working Group.

